There has long been debate over the effectiveness of opportunistic and targeted attacks and how both work. In this blog post I take a brief look at what categorizes an attack.
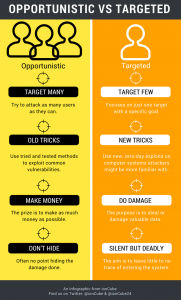
Opportunistic
These are attackers who search for opportunity using a wide range of often well-known exploits to infect as many computers as possible. Vulnerabilities found in outdated software are often the route in, and phishing emails are often the method. A classic example is ‘missed delivery’ spam.
On the whole, the prize is to make as much money as possible meaning the opportunistic attackers often don’t make attempts to hide their actions from security monitoring systems, which means more time and effort for the attacker. One of our particular favourites is the ransomware that just deletes everything, that lacks any form of complexity.
It’s not uncommon for opportunistic attacks to connect compromised computers to form botnet networks, mainly used for DDOS attacks
Targeted
Targeted attacks are easily distinguished as attacks on a specific organisation, often using zero-day exploits to steal or damage valuable data.
The stakes are often much higher with a targeted attack, not only because it’s sourcing specific key information such as employee details or customer bank details, but also because they are likely to be much more experienced hackers who will persistently and silently attack until they get what they want.
Targeted attacks come with a greater level of planning and knowledge since the payload is much greater.
Protect Yourself
- Track suspicious behaviour through the use of logs. It may not be a bug or new feature but a side effect of being hacked. Check for any odd scans coming from outside and inside the network and make sure it’s investigated right away.
- Strengthen your patch cycle, and ensure you are checking every part of your website for vulnerabilities as most attacks on websites are opportunistic. Look at the possibility of getting a pentester to test your website and systems. These are ethical hackers who want to make the cyber world a better place.
- Back it up. Keep a range of well-maintained back-ups.
- Know your stuff. Make sure you and your colleagues are aware of what malware looks like and the forms it comes across in. Make them aware of the “don’t click” rule.
- Get intrusion protection and alerts for your website – which is what we offer with ionCube24.
